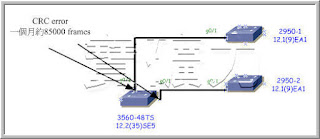
Cisco IOS 12.3在2005年就出來了.
同樣的內容也可以在TechRepublic看到
-------------------------------------------------------------------------------------------------
12 great new features in Cisco IOS 12.3
Version 1.0
Feb. 4, 2005
by David Davis, CCIE, MCSE
There may be a few network engineers out there who jump at the chance
to upgrade Cisco routers to the latest software and drool on IOS
release notes. However, I suspect that for most of you, "investigate
and upgrade to the latest router IOS" is right up there with
"reorganize file cabinet" and "clean out storage room." As a
result, I am willing to bet that most of you haven't upgraded your
routers to the latest version of Cisco IOS 12.3.
The first release of IOS 12.3 was in 2003. Since then, Cisco has made a
number of minor releases that have included some very useful features.
So, whether you don't have any idea what version of code you are
running or you ran out and upgraded to 12.3 when it first came out and
have ignored the subsequent releases, you should take a close look at
the new features that are included in this IOS release.
I am going to highlight some of the major features included in IOS
12.3. I won't talk about the new IPv6 firewall that next-to-no-one is
going to use. Below is a list of 12 features I found most important,
but there are literally hundreds of other features. You can find out
more about the various features in Cisco's IOS 12.3 documentation.
<http://www.cisco.com/warp/public/732/releases/release123/major/>
Author's note: The name of each of the new features is linked to
Cisco's configuration documentation for that feature.
1. Network Admission Control (NAC)
<http://www.cisco.com/univercd/cc/td/doc/product/software/ios123/123newft/123t/123t_8/gt_nac.htm>
Cisco's NAC runs on Cisco routers (running NAC on a switch is coming
soon). With NAC, you also have client software on every PC on your
network (the Cisco Trust Agent). A Cisco Secure Access Control Sever
(ACS) is required to be on the network. Before the PC can have network
access, its antivirus definition version is checked (you can have NAC
check other software versions as well). If the PC does not have the
required version, it is never given access to the network. Instead, it
can be quarantined to a private network to perform the necessary
upgrades. Microsoft has been working on a similar product called
Network Access Protection (NAP). Fortunately, the two companies have
gotten together to try to make their competing products compatible. For
more information on that, read "Cisco and Microsoft Join Forces to Help
Customers Address Security Threats."
<http://www.microsoft.com/presspass/press/2004/oct04/10-18CiscoSecurityPR.asp>
2. Intrusion Prevention System
<http://www.cisco.com/univercd/cc/td/doc/product/software/ios123/123newft/123t/123t_8/gt_fwids.htm>
In IOS 12.0(5)T, Cisco introduced an Intrusion Detection System (IDS).
This version offered only 59 signatures to identify intrusions. These
signatures were not updateable. Thus, as new types of intrusions were
developed, the IOS did not protect against them.
In IOS 12.3(11)T Cisco now offers an Intrusion Prevention System (IPS)
with 118 signatures. The important difference in the new IPS is that it
allows customers to add new signatures as new attacks are developed. It
does this by using a Signature Definition File (SDF), located on the
router's flash. Customers can sign up for new IPS Alerts and read
about existing alerts at Cisco's Intrusion Prevention Alert Center.
<http://www.cisco.com/pcgi-bin/front.x/ipsalerts/ipsalertsHome.pl>
When a packet comes through the router that matches a signature, the
router can be configured to either alert the network administrator or
drop the packet and send an alert. Cisco claims that, due to the new
design, this can be done without affecting router performance.
3. Optimized Edge Routing (OER)
<http://www.cisco.com/univercd/cc/td/doc/product/software/ios123/123newft/123t/123t_8/gt_oer1.htm>
OER is a new feature that allows load distribution at the WAN edge. At
my company, we have two T1 circuits to the Internet running BGP
best-path routing. (I detailed this in "How to use BGP to achieve
Internet redundancy.")
<http://techrepublic.com.com/5100-6265_11-1039765.html>
While it does give us redundancy, it does a poor job of load balancing.
This is because one provider is a Tier 1 and the other is a Tier 2. The
Tier 1 provider almost always offers shorter paths and almost all the
traffic goes across that circuit. We have tried to load-balance using
weight and MED, but it doesn't always work.
OER should be able to solve this type of load-balancing issue. With
OER, you define the policy for your latency, throughput, and link cost
parameters. The router uses this policy to determine how to balance the
load across your multiple WAN links. Most likely, these are Internet
links, but they could be other types of WAN links. OER supports both
static routing and BGP. All this can be configured on the router's
IOS. If you want to have a graphical interface to control a more
complex OER environment, you can buy an add-on OER Linux-based product
called OER Master Controller Engine.
4. Transparent Firewall
<http://www.cisco.com/univercd/cc/td/doc/product/software/ios123/123newft/123t/123t_7/gt_trans.htm>
Say that you want to add a firewall between two networks. Normally,
just like a router, each interface of a firewall has to be on a
different network. This sounds like a large network change, right?
Perhaps it doesn't have to be so complicated anymore.
With IOS 12.3(7)T, Cisco introduced the Transparent Firewall. The
benefits of the Transparent Firewall, as it works at Layer 2, are that
it can be added to an existing network with minimal configuration, and
it provides firewall security for that network. In fact, you can run a
Layer 2 Transparent Firewall on the same router that's running the
Layer 3 Firewall feature. In its most basic form, the Transparent
Firewall works like this: You create a bridge group, put your
interfaces in it, enable "ip inspect" (the firewall) on one of the
interfaces, create an access-list that will be applied to the other
interface, and voila, your Transparent Firewall is done.
5. Warm Upgrade
<http://www.cisco.com/univercd/cc/td/doc/product/software/ios123/123newft/123t/123t_11/gtwarmup.htm>
Warm Upgrade allows a running router to read an IOS image, decompress
it, and immediately boot it. This keeps the router from having to shut
down, go back to ROMMON, load the image, and decompress the image.
Cisco says that this feature, which complements the Warm Reload feature
introduced in IOS 12.3(2)T, will cut down the time for router reboot
from four minutes to two minutes.
6. AutoQoS for the Enterprise
<http://www.cisco.com/univercd/cc/td/doc/product/software/ios123/123newft/123t/123t_11/ft_aqose.htm>
AutoQoS (Quality of Service) is a new feature that discovers the types
of traffic on your network and the speeds of your interfaces, and then
configures the proper network quality for that traffic according to
best practices. This feature is primarily designed to assist in voice
and video quality over the WAN but can be used for a variety of other
things. AutoQoS can do in a few minutes what it could take a network
expert a few hours to do. The downside is that AutoQoS is not full of
options, it does not react to any future changes in the network, and
once it is configured, you still need a network expert to analyze its
results and make sure that it is working properly.
7. AutoSecure
<http://www.cisco.com/univercd/cc/td/doc/product/software/ios123/123newft/123_1/ftatosec.htm>
AutoSecure analyzes your router's security settings and can make
changes for you. I won't go into detail on AutoSecure because I wrote
a full article on it for TechProGuild called "Automate Security
Configurations with IOS 12.3."
<https://techrepublic-secure.com.com/5143-22-22-21307.html>
8. CallManager Express (CME)
<http://www.cisco.com/univercd/cc/td/doc/product/access/ip_ph/ip_ks/cme32/cme32sa/cme32ovr.htm>
and Survivable Remote Site Telephony (SRST)
<http://www.cisco.com/univercd/cc/td/doc/product/software/ios123/123newft/123t/123t_11/srst32ad/srs_over.htm>
CallManager Express (CME) has evolved from allowing a router to be a
very limited, stand-alone, Voice-over-IP (VoIP) phone system to a
nicely featured small to medium enterprise (SME) phone system (on a
router).
Concerning SRST, picture a large corporation that has a centrally
managed CallManager (a Cisco VoIP phone system) with many remote
locations. At these remote locations, the routers would have SRST
configured so that if the WAN connection to the central CallManager was
lost, the SRST-enabled router could provide limited calling features
for the remote phones.
9. Dynamic Multipoint VPN (DMVPN)
<http://www.cisco.com/univercd/cc/td/doc/product/software/ios122/122newft/122t/122t13/ftgreips.htm>
Okay, you got me: Technically, this feature came out in 12.2(13)T, but
it is so cool that I wanted to point it out. DMVPN allows routers to
dynamically bring up, as needed, VPN tunnels to each other over the
Internet. Better yet, these tunnels require only a very simple
configuration. In the past, to create a fully meshed VPN network, there
would have to be a fair amount of configuration on every router (or VPN
concentrator) for every remote site. As the number of remote sites
grew, these always-up VPN tunnels became very cumbersome to scale and
the configurations were unmanageable. With DMVPN, a fully meshed VPN
network can scale, and VPN tunnels are brought up only if needed.
10. IPSec Stateful Failover
<http://www.cisco.com/univercd/cc/td/doc/product/software/ios123/123newft/123t/123t_11/gt_topht.htm>
This feature does exactly what it says it does. You have two routers,
both with IPSec tunnels, being contacted on the LAN with Hot Standby
Routing Protocol (HSRP). If one router goes down, in either a planned
or unplanned situation, the backup router takes over and the IPSec
tunnels never go down. While this has been available on higher-end VPN
concentrators, including it free in the router's IOS is a very nice
addition.
11. Network-Based Application Recognition (NBAR)
Most routers just look at traffic at Layer 3. With NBAR, a router can
look at Layers 4 through 7. That means that a router can recognize
applications. Once it can recognize the applications, it can then take
some action to ensure that that application gets higher priority, drop
packets from that application, or take some other action. NBAR has been
around since IOS 12.0, but it recognized only a small number of
applications. What is new in IOS 12.3 is that NBAR can now recognize
many more applications and new applications can be dynamically added
using a PDLM (Packet Description Language Module). Cisco regularly
releases new PDLMs for new applications. You can find that list at
their PDLM Web page (valid CCO login required).
<http://www.cisco.com/cgi-bin/tablebuild.pl/pdlm>
12. Cisco Security Device Manager (SDM)
<http://www.cisco.com/en/US/products/sw/secursw/ps5318/>
SDM is a free Java management tool for routers. It requires IOS 12.2 or
12.3, depending on your router's model. I did a full article on SDM
so I won't go into what it offers. For more information, check out
the TechProGuild article "Use the free Cisco Security Device Manager to
work with routers."
<https://techrepublic-secure.com.com/5143-22-22-21307.html>
Final analysis
I hate to sound like those lawyers on TV commercials pitching their
services, but here are some things you need to know:
Upgrading your IOS requires that you are either under Cisco SmartNet
Maintenance program or you buy the latest IOS from a Cisco reseller.
Some of the features mentioned here are available only in certain
versions of the IOS. That version of the IOS may not function on all
routers due to CPU, RAM, and flash requirements. Visit the Cisco IOS
Upgrade Planner (valid CCO login required) to see the latest version of
the IOS that your router supports.
<http://www.cisco.com/cgi-bin/Software/Iosplanner/Planner-tool/iosplanner.cgi?majorRel>=
Once you know the latest IOS that your router supports, you can find
out if the features you want are in that IOS. To do that, browse the
release notes for that IOS at Cisco IOS New Feature Documentation.
<http://www.cisco.com/univercd/cc/td/doc/product/software/ios123/123newft/index.htm>
Perhaps there are some features in IOS 12.3 that can make your life
easier or make your network more secure. I have ordered additional
flash memory for my core Internet router just to do the upgrade and get
the OER routing. I hope that you find some of the new Cisco IOS
features as exciting as I do. Upgrading your Cisco routers may seem
like a pretty mundane chore, but the new features make it well worth
the effort.
Additional resources
Cisco IOS 12.3 Major Release page (Flash presentation and a 40-page
PowerPoint)
<http://www.cisco.com/warp/public/732/releases/release123/major/>
Cisco IOS 12.3(11)T Release page (Flash presentation, video, and
customer Q&A)
<http://www.cisco.com/warp/public/732/releases/release123/123t/>
TechRepublic: Cisco Internetwork Operating System (IOS) Fundamentals
<http://techrepublic.com.com/5138-6249-729126.html>
ITPapers: Cisco Internet Operating System
<http://itpapers.techrepublic.com/abstract.aspx?docid=46092>
ITPapers: How to Choose a Cisco IOS Software Release
<http://itpapers.techrepublic.com/abstract.aspx?docid=99777>
Version history
1.0
Bug fixes - None
Feature changes - None
To see more downloads and get your free TechRepublic membership, please
visit
<http://techrepublic.com.com/2001-6240-0.html>







.jpg)